Startup is a vulnerable machine from TryHackMe that was rated as easy difficulty.
As usual we start by scanning the machine for open ports using nmap.
Command: nmap -sC -sV $IP
As we can see we have 3 open ports:- port 21 FTP
- port 22 SSH
- port 80 HTTP
First we are going to start with the FTP because it has anonymous login.
We need to download the files locally by using the next command:.Command: mget *
Reading the notice.txt message we can't see something important. The .test.log file has nothing important.
Let's move on to port 80. Looks like the website isn't ready yet.Next I started a gobuster scan to find some directories.Command: goubuster dir -u $IP -w /path/to/wordlist/ -x /ext. type/
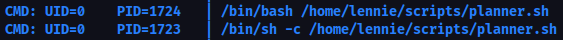
Let's check the /files directory.This looks very familiar to the ftp content and that's because it is the ftp content. The next thing that I tried was to put my file to the ftp shares.As you can see, I created a file called linked.txt and I've uploaded it to the ftp shares using the put <filename> command. The file uploaded by me can be accessed from the website as can be seen from the image below.Now the next step is to get a reverse shell on the box and for this we need to do the same thing we did with the txt file, but this time we will upload a php file.Now if we start a netcat listener on the local machine and click the shell.php file we will get a reverse shell on the client's machine.If we go to "/" directory, we can find the answer to the first question inside the recipe.txt file. Also here we can see the /incidents directory that contains a .pcapng file. Pcapng files can be opened using Wireshark.I transferred that file to my machine so I can analyze it. Now if you follow the TCP stream on the sniffed traffic, you will find the password for user lennie.Shell as lennieNow that I have a shell as user lennie, I used a software called pspy64 to check the running processes on the machine.Looks like we have one process that is executed every minute by user root. Let's check the content of that file.Sadly we can't add our reverse shell command here because we don't have the permissions to write to the file, but we can see that there is another file that is execute: /etc/print.sh
We can see that this file is owned by user lennie, so we can edit it , and that's what I did, I added my own reverse shell command to it.



















Comments
Post a Comment