My School: 1 is a vulnerable machine fromVulnHub that was rated as intermidiate difficulty.
As always we star by scanning the box for open porst.
Command: nmap -A $IP
Let's start with port 80 where it looks like that we have a CMS named Made Simple.The only interesting thing here is that you will found a username: armour, but this won't help us.I tried to brute force the /admin page, but I had no luck.Let's check the next http port, 8080.Now here comes the juicy part. From the image above we can see that we have a wordpress installer page. This will give us the opportunity to connect to our on database.
The first thing we need to do is to start our mysql service.
Command: service mysql start
Now restart the mysql service.
Next I installed the WPTerm plugin (because it's easy to get a shell using it) to get a shell on the box, you can use any method you want to get a reverse shell. I used the python reverse shell command because that worked for me.Now we have a shell on the box as user www-data.Command: service mysql status
Now that our mysql service is up and running, let's create new database and an user.
Commands:
- CREATE USER 'linked'@'%' IDENTIFIED BY 'linked123';
- CREATE DATABASE pink;
- GRANT ALL PRIVILEGES ON pink.* TO 'linked'@'%';
- FLUSH PRIVILEGES;
linked --- is the username
linked123 --- is the password
pink --- is the database
Note: You'll need the above information to connect from wordpress
Command: service mysql restart
Before connecting to our database we need to do one more thing, we need to modify the bind-address, so that we can access the database from wordpress, because as default we can connect to mysql only from localhost.
You need to modify the 50-server.cnf file located in /etc/mysql/mariadb.conf.d
As you can see from the below image we have connected to our database.
Let's keep going. Now we need to create the account for the wordpress service, this should be easy.You need to modify the 50-server.cnf file located in /etc/mysql/mariadb.conf.d
Note: restart the mysql service
With everything modified we can get back to wordpress. Here you insert the neccessary details to connect to the database.In /var/www/html/cmsms/config.php we can find some credentials.
If we used the password from there (/var/www/html/cmsms/config.php) and the username armour, we can get a shell as user armour.
Never heard of rclone, but after some documentation and some trial and error I've found out that I can get a root shell by adding a user to /etc/passwd.First create the same passwd file as the one on the machine, let's call this fake passwd.
Then use openssl to generate a hashed password.
Then use openssl to generate a hashed password.
Comamnd: openssl passwd 123
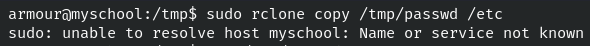
Add a new user to the fake passwd.Now send the fake passwd to the client's machine and then use rclone to replace the real passwd.
Command: sudo rclone copy /tmp/passwd /etc
And now login with the user that we added to passwd, for me being user admin with password 123.
This was a very interesting box!And now login with the user that we added to passwd, for me being user admin with password 123.




















Comments
Post a Comment