Hogwarts: Bellatrix is a vulnerable machine from VulnHub that was rated as medium difficulty and it's the second box from the Hogwarts series.
As always we start with an nmap scan to check the open ports.
Command: nmap -sC -sV $IP
The ssh service is no use to use now because the version is up-to-date and we won't find any vulnerability, alfo we don't have any credentials. Let's check port 80.Here we'll find a gif and some weird text. Let's see what the page source says:
This and the main page gives us a lot of hints. We can see that the "ikilledsiriusblack" repeats itself, but at the end of if there is a ".php". We can visit the page /ikilledsiriusblack.php ,but that is actually the main page. If we check the page source again we can find something interesting.
Looks like that we can use the file parameter to do some "magic". Let's check for LFI.Nice, we have LFI, let's see what else we can read.Ooo, this is big, we can read /var/log/auth.log. We can try some ssh log poisoning. here is a link for you to check on how that works: https://www.hackingarticles.in/rce-with-lfi-and-ssh-log-poisoning/First we login to the client's machine via ssh as user:'<?php system($_GET['c']); ?>'
Now if we scroll at the bottom of the page we'll see the result of our command executed:Rev. shell command link: https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md
Use one of the commands from the link above to get a reverse shell, but first you need to URL encode the command. Here is the link to encode the command: https://www.urldecoder.org/
Now in the browser access the following link: http://$[Machine IP]/ikilledsiriusblack.php?file=../../../../../../../../../../../var/log/auth.log&c=[URL encoded rev. shell command]
Note: remove the square brackets ([ ]) from the link
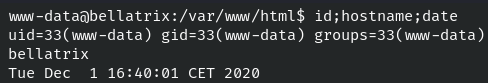
As you can see below we have a shell as www-data
If we do a file listing we can see that there is a directory which name is base64 encoded.The decoded name translates to "secret"
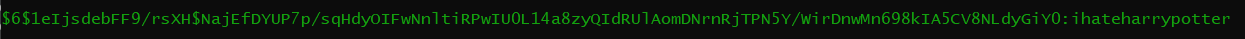
Inside the directory there is a file with the hashed password for user lestrange and a dictionary file.
If we do a file listing we can see that there is a directory which name is base64 encoded.The decoded name translates to "secret"
Inside the directory there is a file with the hashed password for user lestrange and a dictionary file.
We will use the dictionary to to crack the password using hashcat.
If we du a sudo -l we can see what are the privileges for this user.Nice, we can use vim to privilege escalate to root.Shell as root















We can't understand nothing on the upload reverse shell...
ReplyDeleteme too i can't understand nothing
ReplyDeleteI modified the write up. I added the part on how to get reverse shell.
ReplyDelete