NerdHed is a vulnerable machine from TryHackMe that is rated as an easy/medium by the box author.
We start as always with an nmap scan to see what ports are open.
Command: nmap -sC -sV $IP
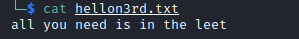
Looks like we have FTP that allows anonymous login. When I see anonymous login, I always check that first. This time I only found a single txt file and an image as you can see below.
This is the image, which is the box logo.
I used exiftool on the image, and one thing stood out, the owner name.
Next thing I did, was to check the SMB shares.
Command: crackmapexex smb $IP --shares -u ' ' -p ' ' --- this will check the shares anonymously (if it is allowed)
I tried to access the nerdherd_classified share but I was not able to, because I was prompted for credentials. I proceeded to check what user are on the box, and I did that by using rpcclient.Command 1: rpcclient -U ' ' $IP
Command 2: enumdomusers
It looks like there is only one user, but this won't help me right now.
Ok, let's move on. On port 1337 we have the standard apache website, but when we access it we are prompted with two messages.
I did a gobuster scan to check for some directories.
Command: gobuster dir -u $IP -w /path/to/wordlist/ -x /ext./
I accessed the /admin directory, but I must say that this is a rabbit hole, because the login page does nothing. Checking the source page we have some base64 text. I decoded the text which was also a rabbit hole.
To be honest I was lost at this point. I asked the author of the box for a nudge and he was nice to give me one: "Look on the things that you may think it is useless".
Now if we go back tot the apache website, we can see that at the bottom of the page there is a youtube link to the song Surfin' Bird by The Trashmen.
I thought that this is just a rabbit hole, but if you think better, if this is a rabbit hole, why this song? Why not a Rick Astley song or some troll face.If you remember, we have found a image on the FTP server that had some random letters as the owner name. Usually random letter could mean one thing: ciphers.
Cipher detect: https://www.boxentriq.com/code-breaking/cipher-identifier
To decode the Vignere Cipher, usually you need a key. Now if you look at the Surfin' Bird lyrics, we can see a sentence that repeats: birdistheword.Now if we use birdistheword as the key, we can decipher the text.I can tell you by now that this is a password. I used the password to check the SMB shares.
Command: smbclient //$IP/nerdherd_classfied -U 'chuck'
Note: Use the password from the cipher when asked for one.
If we access the newly found directory we can see a txt file with creds.
If we access the newly found directory we can see a txt file with creds.
Here is the content of the creds file. For obvious reasons I can't make the content of the file fully readable.
Now we have a shell on the box as user chuck.I used linpeas to scan the machine and immediately I knew what this exploit is: kernel exploit.
If you do a google search against the kernel, you can find that it is vulnerable to dirtycow exploit, exactly to naughtyc0w one. So I used that one.Note: Dirtycow exploit are unstable and can break the machine after a short time.
Exploit: https://github.com/kkamagui/linux-kernel-exploits/tree/master/kernel-4.4.0-31-generic/CVE-2016-5195
Download the exploit and compile it: gcc naughtyc0w.c -o naughtyc0w -lpthread -w
Send the exploit to the vulnerable machine and execute the next command: ./naughtyc0w /usr/bin/passwd
Note: You don't need the compile.sh file
There is a more stable exploit: https://www.exploit-db.com/exploits/45010 . You can use this one to get a root shell and it won't break the machine.
There is a more stable exploit: https://www.exploit-db.com/exploits/45010 . You can use this one to get a root shell and it won't break the machine.


























Comments
Post a Comment