aMaze is a vulnerable machine from VulnHub that is rated as medium difficulty.
As always we start with an nmap scan do discover the open ports.
Command: nmap -sC -sV $IP
First I'll check the FTP because it has anonymous login.It looks like there is nothing on the FTP shares, so let's move to port 80.It looks like we are not allowed to view this page on port 80. Either way let's do an gobuster scan maybe we'll find something useful.Command: gobuster dir -u $IP -w /wordlist -x /extensions -t 50
Just a login and logout page, but I am going to tell you that this is a dead end, so we'll move on.The next port is port 8000 which is also a HTTP server, so let's check it out.
Looks like it's running the Jenkins service. I googled some default credentials for Jenkins and I managed to login by using jenkins:jenkins as username and password. I think there is also a metasploit module that you can use to brute force the credentials.Here is the command used to get a reverse shell
Shell as rootEven if we got a shell as root, we are not actually on the main host machine, but in a docker container, which we need to escape from.If we go to the /root directory, we can see that there is a .git folder.
To check what is inside the git repository, we have to use some git commands.Command: git log
It looks like something was deleted from the machine, let's see what it was.Command: git show
We have to use that token to login to some github repository. You can check the following link for more informations: https://developer.github.com/v3/auth/Command: curl -H "Authorization: token 512fb73b2108f9c882fe3ff559ef4bc9496f4dc2" https://api.github.com/user
Looks like that on the bio there is a pastebin link, let's see what is there.Hmmm, and RSA key, but for what? We'll come to this key in a bit, but for now let's move on.We know that we are in a docker container, so let's check maybe there are other containers. First let's see what is our IP address.
Now let's scan for other machines. To do that there are a lot of methods, one of them being metasploit, but I chose to use netcat to scan for port 22 (SSH) on the other IPs.Command: for i in $(seq 1 10); do nc -v -n -z -w 1 172.17.0.$i 22; done
Looks like there are two more IPs on the same network. I assume that the .0.1 is the gateway so I will connect to the other one. To connect to 172.17.0.3 we need to used the RSA key. We will connect from the machine that we have a shell on (not our own machine).Note: You can do this connection in other ways, one of them is by using metasploit to use port forwarding.
Shell as root
As you can see below we can run the docker to check the list of commands.
But when we try to list the containers, there is a problem.Now if we check the path /var/run/ for docker.sock, it looks like it's missing.Let's find docker.sock.Command: ssh -i id_rsa root@172.17.0.2
And once again we are inside another docker. Now if we ho to /root directory we can find a docker SUID file that can be executed.As you can see below we can run the docker to check the list of commands.
Command: find / -iname docker.sock
Now that we know where the socket is and we know that we have SUID docker, we can try to privilege escalate. Going on gtfobins, I've found that there is a method to exploit docker using SUID.
Now that we know where the socket is and we know that we have SUID docker, we can try to privilege escalate. Going on gtfobins, I've found that there is a method to exploit docker using SUID.
This is the command: ./docker run -v /:/mnt --rm -it alpine chroot /mnt sh
But this command won't work because we are missing something, We need to use the -H flag to specify the daemon socket. You can check the command below.
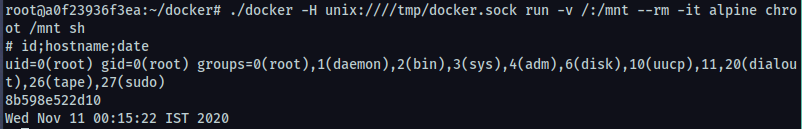
Command: ./docker -H unix:////tmp/docker.sock run -v /:/mnt --rm -it alpine chroot /mnt sh
Now there is only one thing left to do: getting a proper shell on the machine.First create a password using openssl.
Command: openssl passwd -1 1234
After that you can add the password to user andrew, like so:
























Comments
Post a Comment