Cheesey: Cheeseyjack is a vulnerable real-world-like box from VulnHub which was rated as easy-medium.
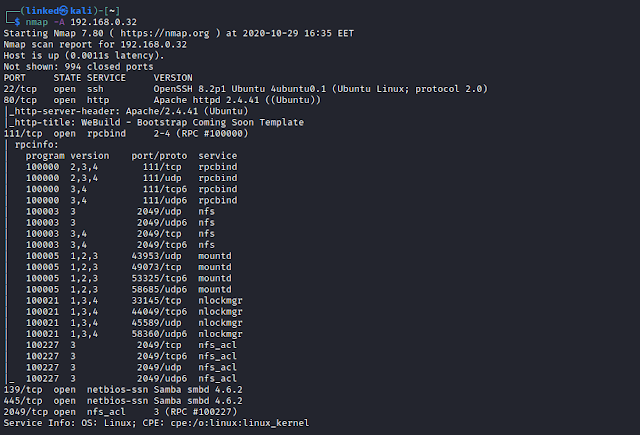
We are going to start with an nmap scan to discover open ports.
Command: nmap -A $IP
Open ports:
- port 22 SSH
- port 80 HTTP
- port 111 RPCBIND
- port 139 and 445 SMB
- port 2049 NFS
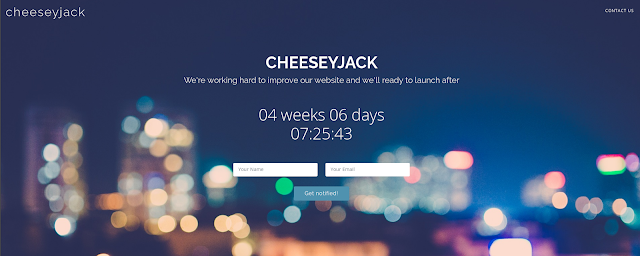
Visiting the website, we don't have a lot of information, just a static page with a countdown timer.
If we scroll to the bottom of the page we can see that we have a DNS which I added to /etc/hosts.
I listed the SMB shares but there was nothing important.
Command: smbclient -L //192.168.0.32/
I did the same thing with the NFS share, but this time I've found a directory.
Command: sudo showmount -e cheeseyjack.local
I mounted the NFS share,but there was nothin important there, so I moved to the next thing.
Command: sudo mount -t nfs 192.168.0.32:/home/ch33s3m4n /mnt/file/
The next thing to do was to start a directory discovery.
Command: gobuster dir -u $IP -w /path/to/wordlist -x /extenstion/type -t 50
On /it_security was a note file from a pentester that stated that the password for user cheese was a weak one.
After I accessed /project_management I was greeted by a login page.
On the box page from vulnhub, the box creator gave a hint:
I took his hint and I created a wordlist from the login page by using cewl.
Command: cewl -d 3 -m 4 -w /save/to/wordlist http://cheeseyjack.local/project_management/index.php/
After that I intercepted the login request with BurpSuite and I did the password brute force with Intruder.
Note: The user is ch33s3m4n (you can find it from the listed NFS shares) and the full username to login is ch33s3m4n@cheeseyjack.local.
And now we can login to the website.
To get a reverse shell was easy. All I had to do was to add a new project in the projects tab and the php reverse file was uploaded on the attachments tab after I was prompted with a new window.
The uploaded files can be accessed from: http://cheeseyjack.local/project_management/uploads/attachments/
Shell as www-data
In /home/crab there is a todo.txt file that tells us that there is a backups SSH key in /var/backups.
And indeed there was a SSH key there. I used the key to login as user crab.
Shell as crab
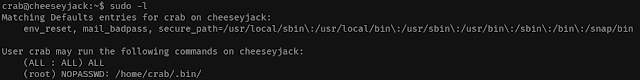
The first thing I do when I get a shell on a machine is to check the user privileges, and luckly there were two.
If we take a closer look we can see that we can execute commands as root in /home/crab/.bin/. That means we can create files in there and execute them as root. And this is what I did.
On my machine I created a file written in C that spawns a shell when is executed. I compiled it with gcc and sent it to the client machine.
On the client machine I made it executable and ran it as root.
Command: sudo -u root ./exp
I hope you enjoyed the write-up and maybe you've learned something new!
















Comments
Post a Comment